Art of Work
Secure Friendly - Budget Conscious Threat Modelling Smart Home
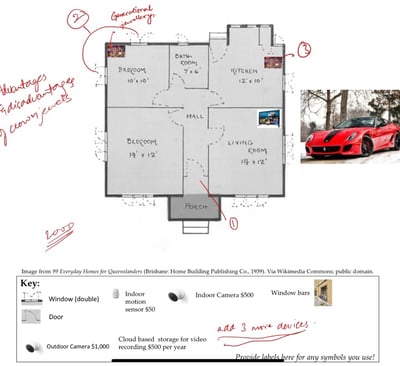

1. Threat Identification: Cataloged key assets within the home, such as heirloom jewelry, cars, and personal safety, this allowed us to tailor our security measures for protection.
2.Vulnerability Assessment: Assessed potential entry points- doors, windows, and other access areas using STRIDE to calculate risk and enhance physical security to thwart unauthorized entries effectively.
3. Strategy:
Physical Security: Installed motion detection cameras and entry sensors at entry points, reinforced windows with metal bars and glass break sensors, and advanced locks.
Digital Security: Prioritized backup to secure cloud storage, allowing for redundancy and remote monitoring.
4.Cost Management: Ensured the security upgrades were cost-effective, ensuring a balance between effectiveness and affordability.
5.Red Team Pentest: Simulated potential attack methods on the house to test effectiveness of security measures and identify any weaknesses in the system before real threats could exploit them.
The most inventive and cost-effective strategy I developed was the "Defense by Hide" approach. Faced with the challenge of securing a valuable Ferrari without available garage space, I devised a solution using a portable, economical tent. This clever concealment not only hid the car from view but also effectively deterred potential thieves.
Exploring Healthcare Ransom Justifications - Why $100,000 and not $10,000?


1. Research Question and Motivation: I explored what drives the demand and payment of ransomware in healthcare. My interest stemmed from vulnerability of hospitals due to their critical data and assumed weak cybersecurity defenses.
2.Study Design and Data Collection: Initially, aim was to compare ransomware demands across countries. However, due to data limitations, I refocused ransom demands only in the US from 200+ affected hospitals.
3. Findings: My analysis showed that ransom demands are influenced by the organizational size and the nature of the data held. Larger hospitals and those with sensitive data tended to face higher ransom demands.
4. Challenges and Insights: I encountered challenges with data scarcity and unique case complexities, which limited the depth of analysis. However, the study's insights emphasized the importance of robust cybersecurity measures and effective incident response strategies.
5. Conclusions and Recommendations: My research confirmed that ransom demands are tailored to the victim’s data value and organizational size. I recommend that healthcare facilities enhance their cybersecurity defenses and develop clear strategies for negotiating with cybercriminals.
Problem
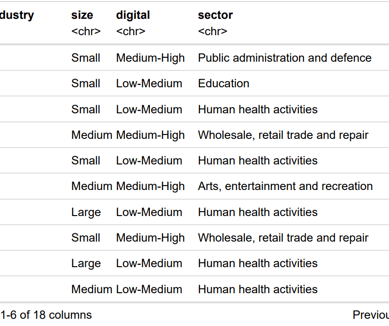
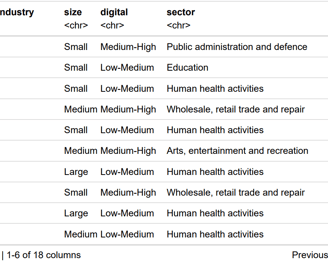
I conducted an in-depth statistical analysis of ransomware attack data using R to uncover patterns in ransom demands across different industries and company sizes. The primary objective was to identify key factors influencing the amount of ransom requested by attackers, which could inform more targeted cybersecurity measures.
Methodology to solve
Data Cleaning and Preparation
Descriptive Statistics
Visualization
Statistical Modeling
Inference Statistics
Results:
Variability in Ransom Demands: There was substantial variability in ransom demands, with certain industries and larger companies frequently facing higher demands.
Impact of Company Characteristics: Statistical tests indicated significant effects of company size and industry type on ransom amounts. Notably, larger companies and those in critical sectors faced higher ransom demands.
Predictive Modeling: Regression models demonstrated that factors such as industry type and company size were significant predictors of ransom amounts. These models could potentially be used for predicting ransom demands based on company characteristics.
Healthcare statistics in R
Blow up that BOILER! - Pen testing


1. Reconnaissance: Explored the target system, focusing on identifying multiple vulnerabilities within the SCADA system website such as open ports using NMAP, inspecting code etc.
2. Gaining Control: Multiple techniques were employed to gain deeper access to the system. This included trial and error using injection, methods where attempts were made to log into the system, which led to the discovery of a printed error message indicating "Password incorrect." This clue suggested that the system might be vulnerable to brute force or dictionary attacks due to its verbose error messages and indicating username is correct.
3. Execution and Monitoring: A dictionary attack was launched against the system. This method proved successful, revealing the correct password, which allowed for unauthorized access into the SCADA system, specifically the SCADABR interface.
With access to the SCADABR system, we could manipulate its controls. We initiated a DoS attack on the Boiler IP address, with initial control over the boiler pressure gained , timed the valve to open, resulting in increased boiler pressure which simulated a critical failure scenario. This ultimately resulted in the boiler "blasting" in a controlled and monitored environment.
Enhancing Cybersecurity Data Analysis Using R
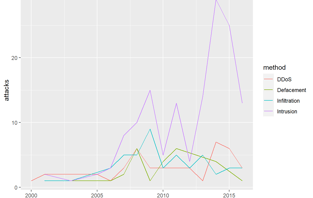
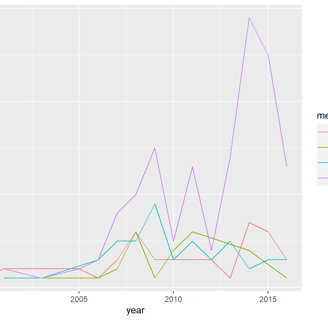
I explored integrating advanced R packages to enhance data analysis in the cybersecurity field. R was used to analyze cybersecurity datasets, including logs, threat intelligence feeds, and security attacks in various countries.
Data Manipulation & Analysis: The analysis focused on cleaning, transforming, and preparing the data using the dplyr package, which is ideal for such tasks due to its capability to manipulate large datasets efficiently.
Data Visualization: I create advanced visualizations with ggplot2 and ggpubr to effectively represent patterns and threats found in the data and to perform statistical modeling and interpretation with Stargazer to identify patterns and anomalies that could indicate potential security risks.
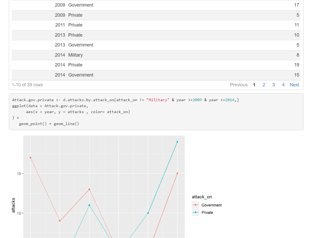
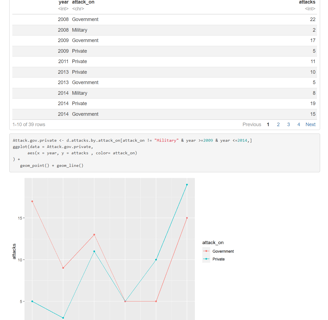
The Problem: "Imagine being unable to reach the light switch on the wall due to various inconveniences. Not everyone can afford to replace their existing appliances with smart devices."
Solution: "Xtend is a game-changer—it's a simple, wireless device that attaches to any existing fan or light and makes it smart. With Xtend, control the appliances directly from your smartphone or through voice commands. And the best part? It installs in minutes and doesn't require any rewiring or professional help."
Market Potential and Strategy: "The smart home device market is expansive yet costly. With Xtend, homeowners, renters, and even commercial properties can upgrade at a fraction of the cost of traditional smart home solutions.
Financials and Ask: The $250,000 investment will be used for scaling production, marketing to reach broader demographics, and enhancing product development."
Did we get the Money? YES! YES!YESSS!!!
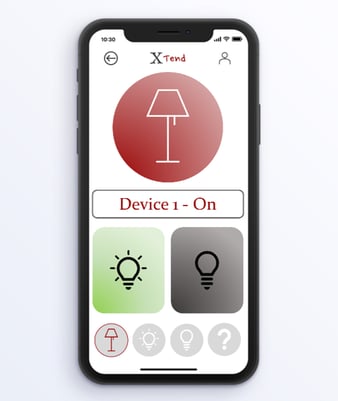
XtenD : Shark Tank @ UTD
CEO: Sahana Pujar
